CrowdStrike CEO George Kurtz: Microsoft’s ‘Failures’ Put Everyone At Risk
In an interview with CRN, Kurtz said the recent Microsoft cloud email breach and frequent bypasses of Microsoft Defender by hackers are just two symptoms of the tech giant’s massive cybersecurity problem.

Kurtz On The Record
The breach of Microsoft cloud email accounts belonging to multiple U.S. government agencies, discovered in June, is just the latest high-profile indicator that Microsoft’s “architectural flaws” pose a massive security risk that few can ignore, according to CrowdStrike CEO George Kurtz. While Microsoft’s strategy of bundling numerous applications and security tools into Microsoft 365 software licenses has proven appealing to many cost-conscious customers, a growing share of organizations are recognizing that the security trade-offs are not worth it, Kurtz said in a recent interview with CRN.
“[It’s] death by a thousand cuts,” he said. “It’s the technology which is insecure, which is your zero-day Tuesdays. It’s things like the U.S. government being breached because of Microsoft’s failures. There’s only so many opportunities to say, ‘Hey, you get it for free, use it’ when people are saying, ‘Well, you’re putting us at risk.’ And that’s really what we’re hearing from customers—Microsoft is putting them at risk.”
[Related: CrowdStrike Reports Surging Adoption Of Identity, Cloud Security Tools]
That holds true not only for Microsoft’s productivity software and Windows operating systems, but also for its Defender security tools, Kurtz said. According to CrowdStrike findings, in 75 percent breaches of Microsoft customers that CrowdStrike’s incident response team has investigated over the years, Defender was in use but was bypassed by attackers. “It really is the fox guarding the henhouse,” Kurtz said. And, he added, it’s proven to be a major source of new business for CrowdStrike, which competes with Microsoft on endpoint security and increasingly in a variety of other categories. “We routinely convert customers that have been breached using Microsoft security technologies into CrowdStrike customers,” Kurtz said.
Ultimately, Microsoft security issues “are putting millions and millions — tens of millions — of customers at risk,” he said.
In a statement to CRN, Microsoft said that “cybersecurity is a top priority for Microsoft and has been for over 20 years.” Additionally, “we believe collaboration and partnership across the security industry is essential to stay ahead of expansive advanced threats and find the
aggressive competitive framing of security issues unfortunate,” Microsoft said.
Chorus Of Critics
While Kurtz has been a vocal critic of Microsoft in recent years — in the wake of widely felt attacks that exploited its technology such as the SolarWinds compromise — he’s far from alone in that regard in the cybersecurity industry. In an interview with CRN in August, Tenable CEO Amit Yoran pointed to a “pattern of behavior” from Microsoft that “undermines security” — and in a LinkedIn post at the same time, accused Microsoft of “grossly irresponsible” handling of a critical Azure vulnerability. And earlier this month, Wiz CTO Ami Luttwak told CRN that Microsoft still has many troubling questions to answer over the cloud email breach that impacted U.S. government accounts. The breach, which reportedly affected agencies including the State Department and Commerce Department, has prompted U.S. Sen. Ron Wyden to request a federal investigation to determine “whether lax security practices by Microsoft” led to the hack.
In speaking with CRN, Kurtz said incidents such as the breach are nothing short of “scary,” given what they show about attackers’ ability to exploit Microsoft security weaknesses.
SMB Push
Kurtz, who co-founded CrowdStrike in 2011, also discussed the cybersecurity giant’s push into the SMB market with the help of channel partners. Increasingly, that will include MSPs, thanks in part to CrowdStrike’s “game-changing” partnership with cloud-focused distributor Pax8, Kurtz said. CrowdStrike has also released Falcon Go—a more affordable version of its acclaimed Falcon security platform—which offers the “core elements of what’s needed [by SMBs] in terms of prevention and visibility,” he said.
During the interview, Kurtz also discussed CrowdStrike’s growing reliance on channel partners overall for enabling the company’s growth streak to continue. The Austin, Texas-based company disclosed that annual recurring revenue reached nearly $3 billion as of the end of July, up 37 percent year-over-year, while quarterly revenue beat Wall Street estimates despite the ongoing economic uncertainty. Notably, “most of our new business is coming from partner-sourced opportunities, which is fantastic,” Kurtz told CRN. “We need to expand that out.”
The strategy, he said, is “to continue to invest and enable our partners. And I think that’s an area that we really want to focus on.” On Monday, the company unveiled its new channel program, CrowdStrike Accelerate, which introduces new incentives, improved training and increased support resources for partners. The launch of Accelerate constitutes the biggest overhaul of CrowdStrike’s partner program since it debuted in 2015, the company said.
Kurtz also discussed CrowdStrike’s new generative AI-powered technology, Charlotte AI, as well as the company’s efforts at expanding more broadly within the IT tools space.
What follows is an edited portion of CRN’s interview with Kurtz.

When it comes to preventing breaches, what are the biggest reasons you’d argue CrowdStrike is superior to Microsoft’s technology?
I ask every customer this—it’s a very simple question: ‘When is the last time Microsoft has called you and said you had a potential breach condition?’ I haven’t got one answer— not one. We’ve got an overlay where we’re engaging with customers. And we’re focusing on getting an outcome. The outcome is stopping the breach. If we see something and the company doesn’t take action, we’re on the phone, we’re emailing, we’re engaging with them.Time is a critical element in stopping breaches—seconds matter. And that’s what we do end to end. That’s highly differentiated from Microsoft, or pick any of the other competitors that are out there in our space, because they haven’t built this integrated approach. And candidly, they don’t really have the architecture that gives them the real-time visibility we have.

At your investor day in the spring, you shared a stat that with 75 percent of breaches of Microsoft customers that you’ve investigated, Defender had been in use but was bypassed. Does that continue to be the case?
Absolutely. When we go in and we investigate these attacks—yes, there’s probably some Microsoft technology that got exploited. But a lot of times, it’s Defender that’s actually being used to protect against these attacks. It really is the fox guarding the henhouse. If you look at the latest breaches that you’ve seen in the government space, and you look at some of the certificates that were stolen, and the [attackers’] ability to impersonate other users across the [Microsoft] 365 environment, it’s scary. And that’s a function of some of the architectural challenges that existed pre-2000, in the way Microsoft works and the way [Active] Directory works. Those challenges were just moved and replicated, en masse, into their cloud. So it’s a challenge for many customers. And there’s a reason why we’ve done so well—because we’re not building applications. We’re not building cloud architectures. We’re building security technologies that work across a heterogeneous environment and across all cloud environments. And that’s what customers are looking for.

When you respond to a breach for a customer that had been using Defender, does that often end up leading them to switch to CrowdStrike?
Absolutely. We routinely convert customers that have been breached using Microsoft security technologies into CrowdStrike customers. It’s at a pretty high rate right now and it continues to be a problem for many customers. It’s a routine part of what we do. When we respond, obviously we are focused on making sure we bring the customer back to health. But of course, many times they’re looking at, ‘Well, how did we have a failure?’ And a lot of it points back to the security technologies in use — particularly when they’re thinking that with an [Office 365] E5 license, they’re going to get everything they need to stop breaches — and that’s just not the case.

What about the cost element? Is the full cost of using Microsoft security tools, as you’ve talked about it, also a driver for customers switching to CrowdStrike?
Yes — there’s up to six different [Microsoft security] consoles that are out there. You’re going to need more people to actually operate it because it’s disjointed. You’ve got inconsistent capabilities across things like Mac and Linux. And of course if you have to respond to a breach, that’s going to be pretty costly. So there’s the people aspect, the management aspect, the daily care and feeding of it, which is going to be more. And time-to-value and ease-of-use is critical for customers. And then of course, there’s the catastrophe piece, when customers have a breach. And I think this is one of the areas that I’m not sure if people fully understand — [that] when you look at the core, fundamental technology of Microsoft [security], that’s signature-based technology. They bought an [antivirus] company in 2004. If you run Windows, you’ll see it’s constantly updating its signatures. So if signature-based technology worked so well, there’d be no CrowdStrike. And [Microsoft security] is not focused on stopping breaches in the way it is architected.

Are you expecting to see more partners switching from Microsoft security technologies to CrowdStrike?
I absolutely think so. Because more and more, we’re seeing the crisis in confidence from Microsoft customers—where they’ve had a problem, they had a breach, they read the news. When the U.S. government is being breached because of Microsoft’s own architectural flaws, that’s pretty concerning. And I think you have partners looking at that and going, ‘OK, what else is out there? Maybe there are other things that we need to add to the mix to make sure that these customers stay safe.’
[It’s] death by a thousand cuts. It’s the technology which is insecure, which is your zero-day Tuesdays. It’s things like the U.S. government being breached because of Microsoft’s failures. There’s only so many opportunities to say, ‘Hey, you get it for free, use it’ when people are saying, ‘Well, you’re putting us at risk.’ And that’s really what we’re hearing from customers—Microsoft is putting them at risk.
What do you think Microsoft needs to do to address these issues?
The challenge is, architecturally, this is not an easy fix. You would just have to change too many things. So [instead] it’s bandaid after bandaid after bandaid. So I don’t have the answer, other than that the architecture needs to be relooked at [around] how authentication works in that environment. [Because] when you look at the impact, [Microsoft security issues] are putting millions and millions — tens of millions — of customers at risk.

Earlier this year you interviewed [CISA Director] Jen Easterly, and she spoke about the need for software vendors to ‘own the security outcomes’ associated with their products. Right now it’s more or less optional for vendors like Microsoft to do that, but do you think in the future it might not be optional anymore?
It may not be optional. I think a lot of this momentum around owning the security outcomes is really focused on Microsoft. Microsoft technologies are pervasive. And I think all vendors have a responsibility to be able to protect their customers. There’s no silver bullet. There’s going to be bugs across every technology stack. That’s just the nature of creating software. But making the right decisions — and making the hard decisions — to fix these [security issues] is what I think Jen is referring to. And having some level of accountability in being able to do that. You can’t just blame the government because the government got breached, which is what I’ve seen. It’s been more about the government being breached than the fact that Microsoft had a problem. So you can’t blame others.

In terms of expanding into the SMB market, do you see the potential to do the same thing there that you did for enterprises?
That’s absolutely right. [Cybersecurity] is one of the unique spaces where you can protect the DoD [Department of Defense] and you can protect the smallest little SMB—it basically is the same technology. So what we found is that being born in the cloud, it’s super easy to get an SMB up and running. We remove a lot of the complexity for them. Time-to-value is immediate.
And we’re seeing that in the SMB space, there’s still a very fragmented market of legacy [antivirus] players that are there, and that’s pretty much all they have for protection. And when you offer them something better—when you offer them the ability to make the problem go away and not have to deal with the managing, the care and feeding, and the head count—it’s very, very compelling. So it’s still in the early innings, but it’s such a massive market that I think it will drive growth for many years to come.
Specific to the partner network, bringing on Daniel Bernard [as chief business officer] and really focusing on this SMB space, creating relationships with companies like Pax8, rekindling Dell—this has really been game-changing for us to be able to get into the SMB partner ecosystem and have success there.

What makes the Pax8 partnership so critical to your SMB strategy?
You can’t go to every little managed service provider out there. [Pax8 has] access to 30,000 managed service providers that have relationships in the SMB market. And when you add it all up, it’s the law of large numbers—a lot of little numbers add up pretty quick. And that has been, I think, a tremendous path for us to get to these smaller SMBs — and obviously, smaller managed service provider channel partners that we simply couldn’t [reach] on our own.
Has Falcon Go been another key piece of the puzzle in terms of reaching SMBs?
Yes, which we didn’t have when we started the company. So we’ve been able to take world-leading technology and package it up in a way that makes it super easy for a customer to buy and to consume, and for partners to be able to leverage that and sell that into their customer base. It doesn’t have every bell and whistle of the full enterprise product, which you would expect, but the core elements of what’s needed in terms of prevention and visibility are there. So Falcon Go has been a great addition.

What are your other major areas of investment in partners right now?
From resellers to cloud providers to managed service providers to PC OEMs—there’s an opportunity for all of these various partners to be successful with CrowdStrike. And we’re investing in it. And you can see the investment with [Bernard] being able to create a separate organization, outside the sales organization. Most sales organizations are focused on making their number every 90 days. So the fact that we’ve been able to move this into a separate group, run by [Bernard], and make the investments that we’re making from both a time and dollar perspective I think is really important for partners. We can’t be successful if they’re not, and we need to continue to build out these routes to market now.
We also need to continue to invest and enable our partners. And I think that’s an area that we really want to focus on. We know we can do better there. We’ve got a lot of partners, and we’re growing so fast that we’ve got to make sure that [the partners] are enabled, and they know all of the technologies — they’re trained, they’re certified — and they can deliver the message. Most of our new business is coming from partner-sourced opportunities, which is fantastic. We need to expand that out.
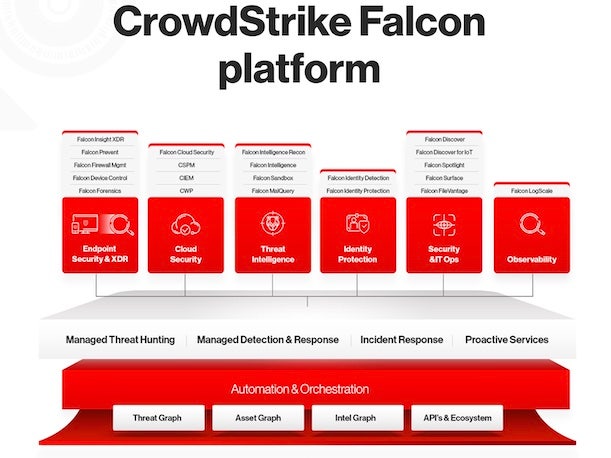
Beyond SMB, what are the other major opportunities for your partners in working with CrowdStrike right now?
We need to empower [partners] and make sure they know about a lot of the other modules, and can sell the other modules, above and beyond the core endpoint protection technologies that everybody knows us for. Identity has been just tremendous, in terms of the adoption—one of the fastest-growing modules we’ve ever introduced.We’ve got LogScale [for] SIEM [security information and event management], which is growing like a weed. [On] cloud protection, we’ve really harmonized cloud workload protection with CSPM [cloud security posture management]. It’s very easy now for customers to consume that. We’ve had tremendous success in those areas. So those are the growth areas that we want to continue to work with.
Could you speak about how CrowdStrike is utilizing generative AI, such as with your Charlotte AI tool?
I think it’s going to revolutionize security. And the biggest area that I see us being able to revolutionize is taking that [Security Operations Center] Tier 1 analyst, and turning that person into a Tier 3 analyst. And taking their job duties, which may be eight hours a day, and allowing them to finish those eight hours in 10 minutes — because there’s just so much point-and-clicking and going through and investigating things. I think what Charlotte is going to be able to do is a take the the the the essence of CrowdStrike’s knowledge, which is a lot — and distill that into an AI technology, which then empowers our customers — and gives them the automation and leverage they need from a people perspective to do more with less, which is incredibly important. And I also think it changes a security workflow from a point-and-click to a generative workflow. [You can] have a conversation with Charlotte — ‘Tell me what the latest threats are? Tell me how that applies to my environment? Tell me the critical assets that they’re on? Generate a PowerShell script, which I can then deploy [as] a patch using Falcon Fusion — and then write a report at the end of the day.’ That would take somebody a whole day to do, that we could do in 10 minutes. We’re really excited about yet again moving the industry in a new direction — similar to what we did with Falcon when we released its initial capabilities centered around AI.

What are your goals right now for expanding more broadly within the IT space, such as into areas like observability?
That’s something we’re continuing to look at in a lot of fine detail. What we found is that with customers who use our technology [for cybersecurity], what happens over time is that the IT teams get wind of this technology and start to ask a few questions. And many times it’s like, ‘I didn’t realize that Falcon can actually do that.’ To give you a good example, in COVID, when everyone had their systems at home, the IT teams were scrambling on how they were going to update the systems and how they were going to reset the passwords. And they were actually using the Falcon technology to administer the systems. So what we found over time is that the IT teams have been wanting more and more of CrowdStrike. They want more visibility into the assets, they want more control. They want the ability to drive automation beyond just security tasks.
And security is a big market, but IT has an even bigger budget.
We’re $100 billion-plus just in security TAM [total addressable market]. If you add IT as a new pool of dollars, it’s massive. So we think that’s really compelling. And we think the ability to leverage this agent is really valuable beachfront that we have. Customers want to do more with less. They want less agents. We’ve got the most-efficient and capable agent out there—it just happens to be that we deliver security through it. But it doesn’t mean that we can’t deliver other IT outcomes using our technology.